



A good way to undermine your “security” brand is to launch a website rife with publicly known exploits.
But how does this even happen? If Rudy Giuliani erred on the side of eye-candy, if he relied on designers instead of infosec specialists, then he’d still have a website built with the most contemporary tools. Designers love new stuff. Instead giulianisecurity.com was built on an end-of-life PHP (5.4) and Joomla (3.1.1). His team exposed LDAP, sshd and mysql — all of which were old and EOL’d.
We can’t trust these people to set up our DVRs, let alone harden our country’s cyber infrastructure. It’s stunning, really.

Stunned security experts tear strips off president-elect pick hours after announcement
Source: www.theregister.co.uk/2017/01/13/giuliani_joomla_outdated_site/
UPDATE: The DNS record has been taken down but you can still reach giulianisecurity.com by it’s raw IP address.
Your JoeDog has been following the President-elect on Twitter for quite some time. He’s a Howard Stern fan and Trump was part of the Howard Stern universe. Then something unexpected happened to this frequent Stern Show guest. He won the presidency. Yep, saw that coming….
So while it’s now possible that a tweet from atop a gilded toilet could touch off a nuclear holocaust and get us all killed, there another more awesome possibility. See, Your JoeDog’s greatest disappointment was his exclusion from Richard Nixon’s Enemies List. He was very young when Nixon left office but that guy was assholish enough to put a child on his Enemies List. It could have happened! Sadly, it never happened. Now according to news reports, Trump blocks people from his Twitter feed. That’s the contemporary equivalent to an Enemies List. Could Your JoeDog get himself blocked???
Now anyone can get on the Presidential Twitter feed and throw some F-bombs and get himself blocked. I was determined to play it clean. Full-frontal snark! I wanted blocked for getting under his skin, like Nixon’s enemies got under his. So how’s that effort going? Sadly, not so good….
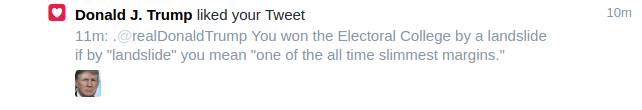
It probably wasn’t an intern who liked that tweet. This appeared in my notifications while Trump was in the midst of a Tweet storm. He was probably scrolling replies and read the first part of a compound thought. “You won the Electoral College by a landslide…” LIKE “… if by ‘landslide’ you mean ‘one of the all time slimmest margins’.” Attention to detail isn’t a trait Americans look for in a President.
You can follow Your JoeDog’s attempts to get blocked by the 45th President @jeffyguy
Well at least it wasn’t Runner1234, amirite?
I do. Sorry been moving. Just in case Milia hasn't gotten it to you let: Apple ID: [email protected] Runner4567
If I was Snowden, I wouldn’t hold my breath waiting for that pardon….

From the article: “As became clear during my investigation over the past three years, nearly every element of the narrative Mr. Snowden has provided … is demonstrably false.”
Source: www.wsj.com/articles/the-fable-of-edward-snowden-1483143143
I don’t think 2017 is going to be much better….

A dog named Scarface attacked his owners after they tried to put a sweater on him.
Remember when Jeb Bush was giving a sad and lonely speech on the campaign trail? He made some stupid point and the audience sat stone-faced as he stood there awkwardly. After what seemed like an eternity, the young Bush hopeful implored his audience to “Please clap.” That’s Your JoeDog right now. But instead of applause, we need you to test the latest siege release candidate. Siege-4.0.3-rc2
We know what you’re thinking: What’s in it for me? Exciting new features, that’s what! Really? Like what?
Well Your Linux distributors should be happy now. For years they’ve been bugging Your JoeDog to eliminate his convenience library. Linux distributors don’t like convenience libraries which is odd because they’re very convenient. With this release, we move that code from lib/joedog into src.
Valery Levental fixed and improved issues involving the data URI scheme, chunked transfers and zero-length content.
Danylo Hlynskyi improved the man page documentation.
[SIEGE: 4.0.2]
Somebody sent Your JoeDog a patch that he promptly lost. If that person could resend it, he’d very much appreciate it…..
UPDATE: Your JoeDog found the patch. It’s a fine piece of work by Valery Levental. The patch tested out and was submitted to version control. In all likelihood, we won’t release a beta distribution. You can grab the code off github.com.
This patch
Some siege users have reported hangs with version 4.x.x This update may fix those conditions (although in some cases, the problem was tied to a specific version of glibc.)
Your JoeDog is pleased to announce the release of siege-4.0.1.
This release contains no recognizable goodies for you to play with but it will probably reduce the number of times you curse at us. It is primarily a bug fix.
You knew that was coming, right? Some of you may have put off the move to 4.x in anticipation of the blessed 0.0.1 bug fix release. Well, here it is!
This release includes a patch by Niklas Hambüchen which improves the efficiency of chunked encoding reads. It also includes a patch by Warren Young which improves / fixes issues with cookie handling and expiration. Trent Oswald included additional default MIME types and V. Filanovsky added support for URLs longer than 4096 characters.
The release also includes several other minor bug fixes and documentation errors.
If you’re running version 4.0.0, then you should probably upgrade.
[SIEGE RELEASE: 4.0.0]