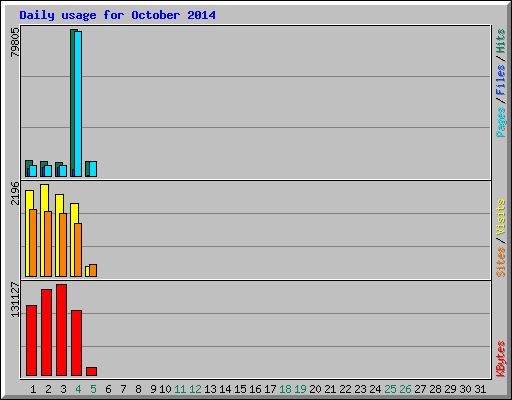
Your JoeDog was viewing his usage stats this morning and … well, see if anything stands out:
There was a 94% increase in traffic yesterday. Was your JoeDog slashdotted? There was no hint that slashdot or any other site sent additional viewers this way. The vast majority of traffic arrived by direct request. “What does that mean, a direct request?” It means somebody typed “www.joedog.org” in the URL field of their browser. “So eighty-one thousand people decided to type “www.joedog.org” in their browsers? That seems unlikely.” That’s what Your JoeDog thought.
The usage report revealed another interesting fact. Eighty-one thousand requests were made from a single IP address: 173.245.50.137. The next most active IP address made 97% fewer requests. That’s interesting. Let’s see was Mr. 173.245.50.137 was doing on this site, shall we?
$ egrep 173.245.50.137 joedog-access_log 173.245.50.137 - - [04/Oct/2014:17:59:48 -0400] "POST /wp-login.php HTTP/1.1" 403 214 "-" "-" 173.245.50.137 - - [04/Oct/2014:17:59:48 -0400] "POST /wp-login.php HTTP/1.1" 403 214 "-" "-" 173.245.50.137 - - [04/Oct/2014:17:59:48 -0400] "POST /wp-login.php HTTP/1.1" 403 214 "-" "-"
He — you know it was a he — was making POST requests to the WordPress login page. In other words, he was running a dictionary attack against the site. This attack persisted for four hours. For each of those requests, apache responded with HTTP-403. “What does HTTP-403 mean?” It means “Forbidden.” Thanks to a dictionary attack defense Your JoeDog documented in June 2013, the attacker never reached the login page. He was thwarted by an apache rule.
Why did a futile attack persist so long?
It was probably launched by malware on a zombie computer. Given the expected number of failures, the program was probably designed to report successes, not denials. So even though its assault was futile, the zombie diligently ran through its entire list of credentials.
When this happens to you — and it will happen to you, don’t get too upset. It’s not personal. These guys are running these attacks on any site they can find. Your site just happened to be in IPv4 address space.
[JoeDog: How To Stop A WordPress Dictionary Attack]